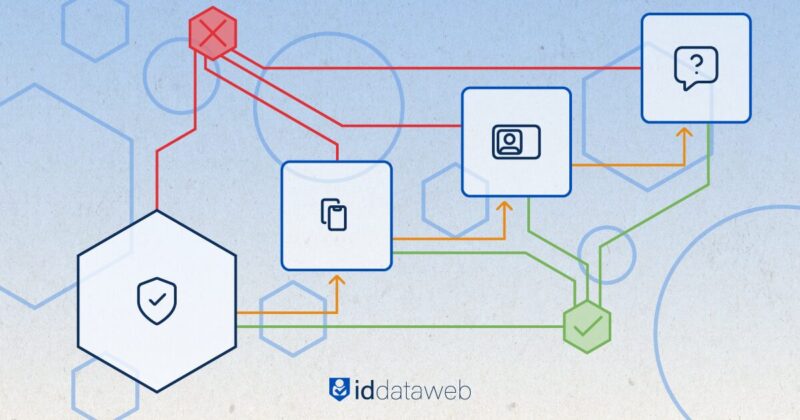
Security architects increasingly recognize that there’s no single “silver bullet” for digital identity verification. Static credentials like passwords—or even standard two-factor authentication (2FA)—were once considered enough, but sophisticated attackers now breach them with relative ease. Modern threats include phishing, social engineering, and SIM-swapping.
In response, many organizations are adopting step-up authentication—an approach that adds more robust identity checks only when certain risk indicators appear.
Rather than imposing high-friction methods on every user, step-up authentication tailors verification to the context of each interaction. In this article, we’ll look at:
- The basics of step-up authentication
- Why risk-based verification is increasingly crucial
- Common methods, from KBA to biometric checks
- Pitfalls of single-method solutions like SMS-only 2FA
- Best practices for automated step-ups
What is step-up authentication
Step-up authentication is a conditional security mechanism that intensifies verification when the user’s activity or profile signals elevated risk.
Think of a standard login as the first checkpoint; if something looks unusual—like a new device or suspicious IP address—the system “steps up” the authentication with an additional factor. This might be an ID scan, knowledge-based questions, or a biometric match.
The benefits of step-up authentication
Tailored security without blanket friction
Adaptive protection: Attackers often rely on the fact that every account or transaction faces the same authentication routine. Step-up authentication counters this by adjusting requirements based on real-time risk signals.
Minimal user disruption: Low-risk logins (e.g., same device, typical location, no suspicious patterns) only require baseline checks, preserving a smooth UX for returning customers.
Reduced false positives and fewer customer drop-offs
Contextual escalation: Instead of automatically flagging borderline cases and forcing manual reviews, step-up authentication gives genuine users a chance to verify their identity through an extra step—like a selfie or brief knowledge-based quiz.
Higher approval rates: Good users who might have been erroneously denied under rigid rules can pass with ease, improving onboarding success and preventing churn.
Stronger fraud deterrence
Second-line defense: Even if an attacker manages to compromise passwords or intercept SMS codes, they still need to clear an extra checkpoint. Methods like biometric checks or official document scans are much harder to fake than a simple code.
Faster response to new threats: Security teams can raise or lower thresholds as fraud patterns evolve—no need for a one-size-fits-all approach.
Common step-up methods and how they layer onto standard authentication
Practically every organization already has a baseline authentication flow in place, such as a username-password combination, potentially coupled with 2FA or an authenticator app.
Step-up methods build on these existing layers, kicking in only when the system flags heightened risk. Below, we explore each method in more depth, including how it works alongside standard practices.
Document verification
The user snaps a picture of a driver’s license or passport; advanced solutions verify security features (like holograms) and compare the ID’s photo to a live selfie.
Benefits: High confidence in identity.
Drawbacks: Requires good camera access; not all users have their ID readily available.
Knowledge-based authentication (KBA)
The user answers queries like their past addresses, last car loan, or other historical data.
Benefits: Familiar to institutions and users.
Drawbacks: Publicly available PII can undermine KBA if attackers gather enough stolen info.
Two-factor authentication (2FA)
The user either receives an SMS or uses an authenticator app to produce a one-time code.
Benefits: Straightforward user flow; widely adopted.
Drawbacks: SMS is vulnerable to SIM-swaps, and app-based codes can be stolen if the user’s device is compromised.
Biometrics and behavioral signals
Biometric software checks for liveness (making sure it’s not just a photo) or matches the user’s typical “usage pattern” gleaned from prior sessions.
Benefits: Very tough for attackers to fake.
Drawbacks: Requires robust tech for capture and matching; user privacy concerns if not handled transparently.
Weaving these methods on top of a standard sign-in, you add multiple lines of defense. Even if one factor is compromised (e.g., the password is stolen), the next factor in the chain is often far harder to fool.
Moreover, the system only dials up friction for users who raise suspicion, leaving the majority free to log in and transact with minimal hassle.
Intelligently automating step-up authentication
One of the greatest advantages of step-up authentication is its ability to be automated, reducing manual overhead while improving both security and user experience.
Below, we’ll look at the three main components of an automated step-up system: dynamic risk scoring, policy configuration, and workflow orchestration.
Dynamic risk evaluation
Dynamic risk scoring uses real-time data to rate the risk level of each user session. Rather than relying solely on static credentials, the system gathers contextual and behavioral signals to build a more accurate profile of whether the user is who they claim to be.
If the risk score crosses a predefined threshold, the platform triggers additional security checks.
Key risk evaluation signals
Device intelligence
- Fingerprinting: Identifies unique device attributes (browser version, plugins, OS details) to recognize returning devices and detect spoofing.
- Known fraud devices: Flags devices already linked to past fraud attempts or blacklisted due to suspicious activity.
Geolocation
- Location matching: Compares the user’s IP address or GPS data to typical login locations.
- Anomaly detection: Flags drastically different regions or the use of TOR/proxy networks known for hiding true location.
Velocity checks
- Burst activity: Tracks the volume of logins or transactions within short time frames. Rapid attempts often signal brute-force attacks or bots.
- Multiple accounts: Monitors for multiple sign-ups from one device or IP in quick succession, hinting at credential-stuffing schemes.
Behavioral analytics
- Keystroke dynamics: Observes typing speed, patterns, and potential copy-paste behavior for anomalies.
- Mouse movements: Identifies human vs. automated inputs (e.g., unnatural, pixel-perfect movement may indicate a bot).
Policy configuration
Policy configuration refers to how your security team defines rules and thresholds for escalating from standard authentication to step-up checks. The ability to quickly adjust these rules is crucial for staying ahead of evolving fraud tactics and user behavior.
Components of policy configuration
1. Dynamic thresholds
- Tightening rules: If a specific geography or IP range sees a spike in fraudulent attempts, security teams can immediately raise risk thresholds, triggering more frequent step-ups.
- Relaxing rules: If false positives climb too high—causing user friction—teams can ease thresholds so that only genuinely suspicious sessions get flagged.
2. Flexible data sources
- Phone porting checks: Integrate APIs that detect recently ported phone numbers—often a strong sign of SIM-swapping.
- Negative lists/blacklists: Continuously update IP, device, and email blacklists to deny or escalate high-risk entities without altering your entire workflow.
3. No-Code/Low-Code Management
- Rapid Updates: Ideally, a policy engine has a user-friendly dashboard. Security teams can modify step-up criteria (e.g., “require ID verification if risk attributes x, y, z are met”) without developer assistance.
Workflow orchestration
Workflow orchestration is the process that ties together dynamic risk scoring and policy rules to automatically route each user session through the appropriate authentication path. It ensures all the checks, prompts, and verifications occur in the correct order and at the right time.
Typical orchestration steps
1. Initial login or transaction
A user enters credentials, attempts a financial transfer, or initiates another action that requires authentication.
2. Risk evaluation
The engine evaluates a risk by analyzing device, location, and behavior signals.
3. Decision to proceed or escalate
If risk is low the user completes the transaction or login with minimal friction. Authentication complete.
If risk is high a step-up authentication challenge is triggered (document check, selfie, KBA, etc.), moving the user to step four.
4. Verification
The user follows the prompt (uploads an ID, answers knowledge-based questions, or takes a selfie). The system validates the response in real time.
5. Outcome
Successful verification: Access granted or transaction approved.
Failed or abandoned: The system may block the request or mark the session for manual review.
How these three pillars work together
When combined, these pillars create an automated system that dynamically adapts to each user’s context. The result is a powerful balance between a low-friction experience for trusted users and airtight security measures for suspicious activity.
- Risk scoring identifies which sessions might need more scrutiny.
- Policy configuration determines the level of scrutiny and which data sources or thresholds apply.
- Workflow orchestration executes the entire process seamlessly, allowing legitimate users to proceed quickly while escalating high-risk attempts.
Conclusion
Step-up authentication offers a dynamic way to guard user accounts and transactions without burying everyone under excessive security hurdles. By activating additional checks only when context demands it—like suspicious locations or unrecognized devices—you maintain a streamlined login flow for most users while locking out bad actors.
If your goal is to secure digital interactions while retaining user trust, step-up authentication should be near the top of your security roadmap.